The Bangladesh embassy in Cairo website is under the control of cybercriminals in a serious case of cryptojacking escalation, according to infosecurity company Trustwave.
The embassy website was first compromised as part of a cryptomining operation in October 2018, the Chicago-based firm says. In January that escalated into almost the entire website being modified to prompt the download of a malicious word document.
Downloading the file installs cryptomining malware onto the victim’s computer, although once the device is infected other types of malware could in theory be installed.
The breach is particularly serious given that the embassy website is a trusted source and receives visitors from government and business officials.
It is also further evidence that cryptojacking – which sees hackers infect victim’s machines with malware to divert computing power to mine cyryptocurrency – is the new favoured method of cyberattack.
Since 2018 cybercriminals have increasingly favoured cryptojacking over ransomware, largely because cryptojacking can operate under the radar and often offers better financial returns.
How well do you really know your competitors?
Access the most comprehensive Company Profiles on the market, powered by GlobalData. Save hours of research. Gain competitive edge.

Thank you!
Your download email will arrive shortly
Not ready to buy yet? Download a free sample
We are confident about the unique quality of our Company Profiles. However, we want you to make the most beneficial decision for your business, so we offer a free sample that you can download by submitting the below form
By GlobalData“Sloppy” work
However, despite the seriousness of the breach, Trustwave’s vice president of security research, Ziv Mador, says that the operation is “sloppy” and “doesn’t make much sense”.
“Given the fact that they were able to hack the web server, they were able to inject a script to that domain and do the mining in a stealthy way like it’s done on hundreds of other websites,” he told Verdict.
“Instead they added that word document, making it very visible, with the same goal at the end of running mining code. It doesn’t feel like the work of a professional team.”
Further suggesting a lack of professionalism is the fact that the word document that users are prompted to download is blank.
“Normally in phishing attacks they would show some content that makes sense in the context of the domain. For example, an embassy site could show the opening hours or the list of consular services that are being provided,” said Mador.
A testbed for something bigger?
That being said, Mador warns that other, more advanced groups, could do something “similar” but implement it in a way that is harder to detect and more dangerous.
“So perhaps they are trying something new, testing the waters, trying some new sequence of infection that they would perhaps eventually use for a different purpose.
“Perhaps this website is a testbed for something bigger.”
One possibility is injecting spying software instead of mining software.
“Because embassies, the people who use their services, might be targeted,” said Mador, citing the murder of journalist Jamal Khashoggi at the Saudi consulate in Istanbul.
The cryptojacking escalation explained
A user downloading the word document would see their computer infected with a malicious EPS file, which exploits a use after free vulnerability (UAF) known as CVE-2017-0261. UAFs are a class of memory corruption bugs that hackers can use to execute arbitrary code on the target computer.
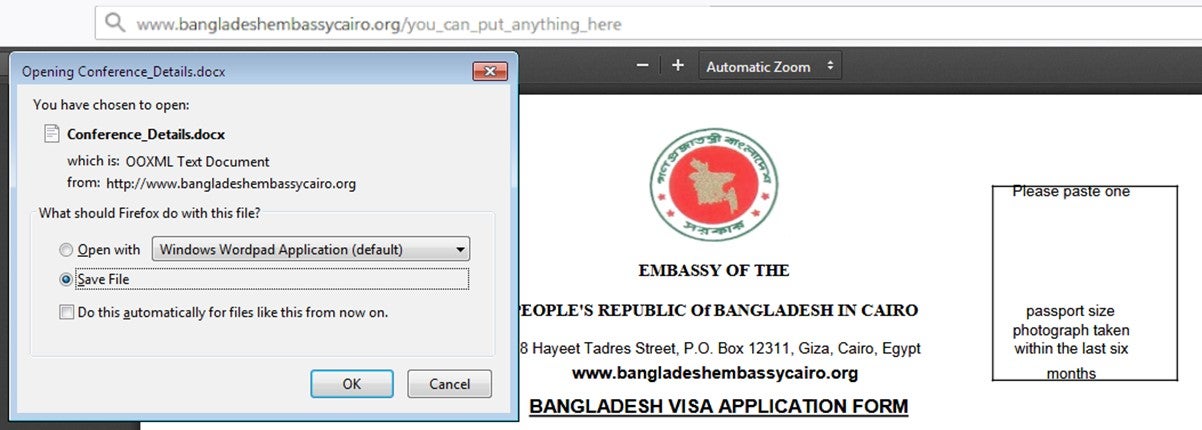
Once this EPS file is executed, an additional vulnerability is exploited, known as CVE-2017-7255.
As soon as the user opens the document, the general purpose malware loader called Godzilla is installed. Once an internet connection is established, the attackers can drop additional types of malware onto the computer – in this case, a cryptominer.
However, Mador says this loader could be “configured or instructed to download anything”.
“The use of a document with an exploit is not new,” said Mador. “The use of a downloader is not new. What’s new here is that they completely reconfigured the web server to return that malicious document from almost any URL that you specify under that domain.”
The vulnerability of embassy websites
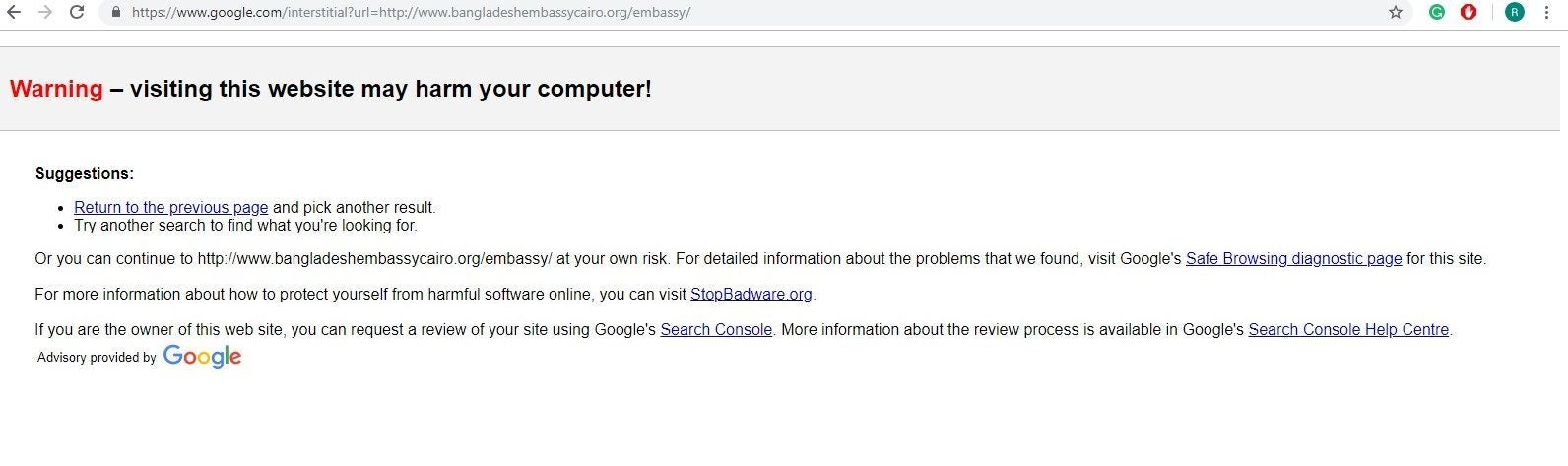
Alarmingly, just three malware detectors flagged the malicious page, with Trustwave being one of them.
“What we learned from this incident is that embassies, in spite of the fact they serve sensitive services or the people using them might be targets, sometimes the security of their websites is not properly maintained. They are vulnerable in spite of the sensitivity and criticality.”
Trustwave said it informed the Bangladesh embassy in Cairo of the attack in January, but the response has been slow.
“When we approached the staff of the embassy they had no clue what was going on there.”
At the time of writing, the website is still compromised. Verdict’s attempts to access the Bangladesh embassy website returned warnings from Google that the site is malicious.
Read more: Is your cloud at risk of cryptojacking?