
Since 2014, Chinese hackers have carried out sustained attacks on companies all over the world via their supply chain.
A new report by PwC’s UK cyber security practice and BAE Systems, compiled with help from the National Cyber Security Centre (NSCS) has been released, detailing what has been going on in what has been dubbed Operation Cloud Hopper.
PwC said the group has conducted “one of the most prolific espionage campaigns”, and have been “employing new tactics to reach a broad audience.”
Since 2016, the two companies have been assessing the victims of the new cyber espionage campaign. Here is what we know about Operation Cloud Hopper.
Who has been involved?
PwC and BAE believe that a group called APT10 has been targeting companies all over the world in sustained hacking attempts.
It is thought that this is a Chinese-based actor, due to the time zones that the group appears to stick to when carrying out campaigns, China Standard Time, as well as the targets.
How well do you really know your competitors?
Access the most comprehensive Company Profiles on the market, powered by GlobalData. Save hours of research. Gain competitive edge.

Thank you!
Your download email will arrive shortly
Not ready to buy yet? Download a free sample
We are confident about the unique quality of our Company Profiles. However, we want you to make the most beneficial decision for your business, so we offer a free sample that you can download by submitting the below form
By GlobalData“The threat actor’s targeting of diplomatic and political organisations in response to geopolitical tensions, as well as the targeting of specific commercial enterprises is closely aligned with strategic Chinese interests,” said the report.
APT10 has been carrying out attacks for a few years now, at least since 2009, but it has grown in sophistication and resources as there was a significant step-up in activity in 2016.
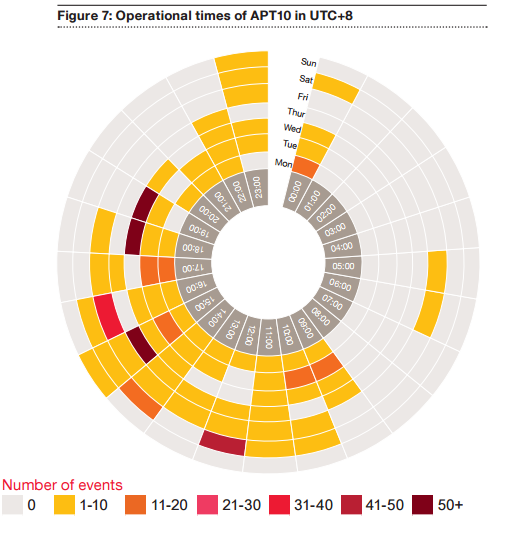
Who has been targeted?
In the past, the APT10 group has targeted government and US defence industrial base organisations and the report believes that this targeting continues. However, Operation Cloud Hopper has been focused on targeting and attacking of managed service providers (MSPs), usually information technology service providers.
“Such providers are responsible for the remote management of customer IT and end-user systems, thus they generally have unfettered and direct access to their clients’ networks. They may also store significant quantities of customer data on their own internal infrastructure.”
As a result, MSPs are a natural target for a hacking group because it will make it easier to gain access to other victims.
“APT10 has been observed to exfiltrate stolen intellectual property via the MSPs, hence evading local network defences.”
The group has targeted sectors including, energy and mining, public sector, pharmaceuticals and life science, and technology; in countries such as, the UK, France, India, Australia, US, Canada, Brazil and Japan.
Why are the Japan attacks so significant?
The report believes that APT10 has been systematically targeting Japanese organisations using bespoke malware. The group has been masquerading as legitimate Japanese public sector entities, such as the Ministry of Foreign Affairs, to gain access to organisations.
“Targeting of these entities by APT10 is consistent with previous targeting by China-based threat actors of a wide range of industries and sectors in Japan. This includes the targeting of commercial companies, and government agencies, both of which has resulted in the exfiltration of large amounts of data.”
What was the nature of the hacks?
APT10 uses a spear phishing email, usually with an attachment designed to lure the target to open it. Those warnings when you get told not to open attachments from emails you don’t recognise? This is when that comes into play.
Here is an example of the malicious decoy documents APT10 was using:

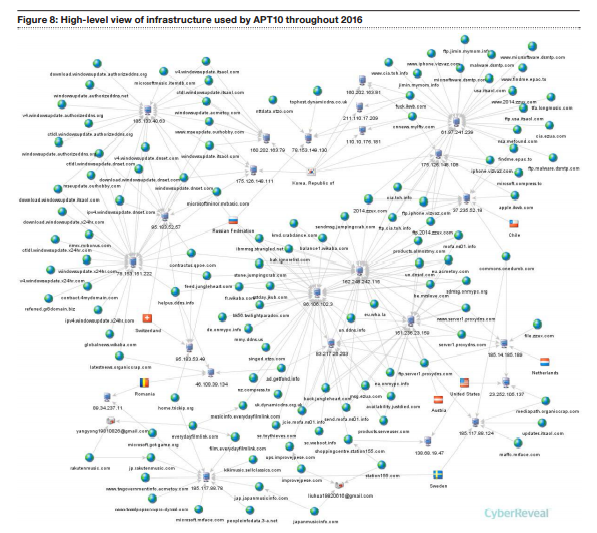
Through this, the group has been able to target intellectual property and other sensitive data from its victims and used compromised networks to move the data around the world.
How can companies stay secure in the face of hacking?
The bottom line of Operation Cloud Hopper is that companies need to ensure they are secure and their third party relations are, both in the supply chain and their cloud providers.
Kris McConkey, partner, cyber threat detection and response at PwC, said:
“The indirect approach of this attack highlights the need for organisations to have a comprehensive view of the threats they’re exposed to – including those of their supply chain. Alongside our research work, we have also notified the threat intelligence community and worked with the NCSC to notify managed service providers and known victims.”
The accounting firm, BAE and the NSCS all worked together to find out as much as they could about the work of APT10 and to inform the companies targeted about what has happened. PwC’s cyber security partner Richard Horne believes that close working collaboration is key to success in scenarios such as this for the future.
“The future of cyber defence lies beyond simple intelligence sharing, but in forging true collaboration between organisations in the public and private sector with the deep technical and innovative skills required to combat this type of threat. This operation has demonstrated the importance of the recently established National Cyber Security Centre, set up for moments just like this.
“Operating alone, none of us would have joined the dots to uncover this new campaign of indirect attacks. Together we’ve been working to brief the global security community, managed service providers and known end victims to help prevent, detect and respond to these attacks,” he said.







