
Two years ago the WannaCry ransomware attack crippled organisations around the world. The malware, which decrypted files on more than 200,000 computers and demanded Bitcoin payment to unlock them, has been on the decline since Microsoft rolled out a security patch and a kill switch limited its spread.
But as WannaCry detections fizzle out, the mechanism that allowed the attack to spread so destructively – EternalBlue – is enjoying a peak in popularity.
The EternalBlue exploit is widely acknowledged to have been developed by the US National Security Agency (NSA) as an intelligence tool. It was allegedly stolen by a mysterious hacking group known as the Shadow Brokers, who in turn unleashed it on the world in May 2017 in the form of WannaCry.
The exploit takes advantage of a vulnerability in Microsoft’s Server Message Block protocol (SMB) via port 445. Computers that have updated with Microsoft’s patch are protected from this security flaw, but data from Shodan, a search engine for looking up internet-connected devices, shows how almost a million machines are still using the obsolete SMB v1 protocol.
EternalBlue: Same exploit, different payloads
In the past, EternalBlue has enabled other high-profile cyberattacks including NotPetya and BadRabbit. More recently, EternalBlue has seen a resurgence in its use to spread malicious cryptominers, which hijack a victim’s computing power to mine for cryptocurrencies.
Because EternalBlue is the gateway, attackers can continue to inject malicious payloads into unpatched machines, even if that isn’t WannaCry.
How well do you really know your competitors?
Access the most comprehensive Company Profiles on the market, powered by GlobalData. Save hours of research. Gain competitive edge.

Thank you!
Your download email will arrive shortly
Not ready to buy yet? Download a free sample
We are confident about the unique quality of our Company Profiles. However, we want you to make the most beneficial decision for your business, so we offer a free sample that you can download by submitting the below form
By GlobalDataWeb Hosting company Eonix Corporation is the organisation with the most unpatched devices, according to Shodan’s data. Amazon comes in at 7th, with 21,090 unpatched machines.
EternalBlue’s growing popularity is backed up by data gathered by cybersecurity firm ESET, which shows a spike in EternalBlue detections at the end of 2018 and early 2019. 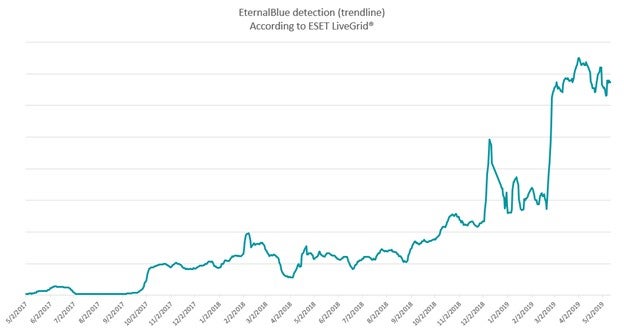
ESET clients reporting attempts to use EternalBlue against them correlate with these findings.
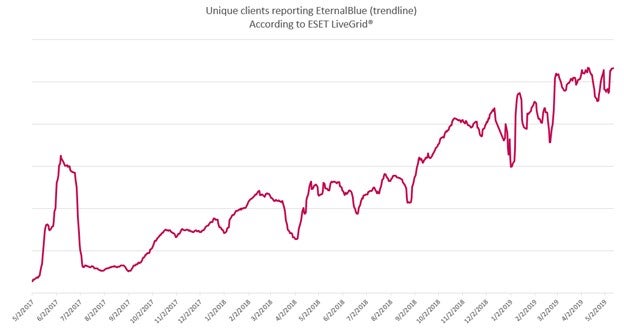
ESET said part of EternalBlue’s rise could be attributed to its use by internal security teams to hunt for vulnerabilities within corporate networks, in addition to new and returning threats.
“This exploit and all the cyberattacks it enabled so far highlight the importance of timely patching,” commented Ondrej Kubovič, ESET Security Awareness Specialist.
“Moreover, it emphasises the need for a reliable and multi-layered security solution that can do more than just stop the malicious payload, such as protect against the underlying mechanism.”
Read more: NotPetya, WannaCry: The privatisation of nation-state capabilities threatens us all



