
The group of malicious hackers behind the British Airways breach made 65,000 unsuccessful attempts to steal shoppers’ payment data in July, according to anti-malware firm Malwarebytes.
Web skimmers, also known as skimmers, sniffers or wipers, sees a malicious hacker insert code into a website to capture sensitive information from online payment forms.
Typically, this means replacing a piece of JavaScript code in a way that blends in to avoid detected for as long as possible.
US-based Malwarebytes said it detected a summer surge of web skimming attempts, with 54% of Magecart activity taking place in the US. The next highest volume of activity was in Canada (16%). Germany, France and the UK accounted for less than 10% each.
There was a peak in activity around the 4 July, indicating that the web skimmers were looking to take advantage of shoppers seeking out Independence Day deals.
How well do you really know your competitors?
Access the most comprehensive Company Profiles on the market, powered by GlobalData. Save hours of research. Gain competitive edge.

Thank you!
Your download email will arrive shortly
Not ready to buy yet? Download a free sample
We are confident about the unique quality of our Company Profiles. However, we want you to make the most beneficial decision for your business, so we offer a free sample that you can download by submitting the below form
By GlobalData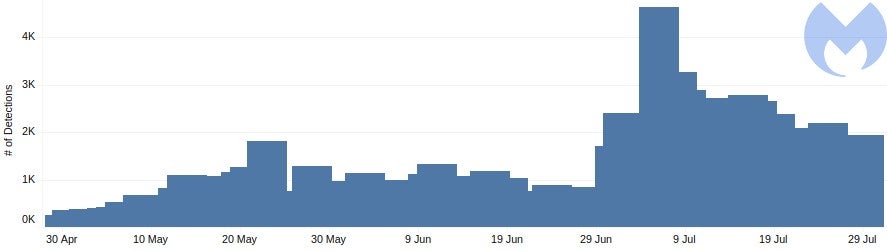
Magecart web skimming shows no sign of slowing
Malwarebytes said its anti-malware software successfully blocked 65,000 attempts to steal credit card details on compromised stores.
Magecart, which is made up of a consortium of hacker groups, has become more prolific in recent years.
Threat research company RiskIQ concluded that the group was behind the 2018 Ticketmaster breach, in which tens of thousands of customers had their payment details stolen.
The 2018 British Airways hack is the most high-profile, impacting 380,000 customers. The attack resulted in a record-breaking £183m GDPR fine.
More recent Magecart web skimming attacks include Forbes magazine’s subscribers and the Atlanta Hawks merchandise store.
In July Amsterdam-based eommerce fraud protection specialist Sanguine Security Labs discovered that 962 online shops had customers’ payment details stolen in a 24 hour period.
Malwarebytes identified Magecart as being responsible by analysing the skimming code used in the attacks. Attribution has become more difficult given that card skimming code kits are sold on underground forums, as well as copycats reusing existing code.
Malwarebytes recommends affected firms file abuse reports with the Computer Emergency Response Team (CERT), and “and working with partners to take a more global approach by tackling the criminal infrastructure”.
For consumers, it’s best to stick to larger, more established shopping portals. However, as shown with Ticketmaster and British Airways, this doesn’t always guarantee safety.
Read more: The rise of Magecart: What do businesses need to know to keep customers safe?



