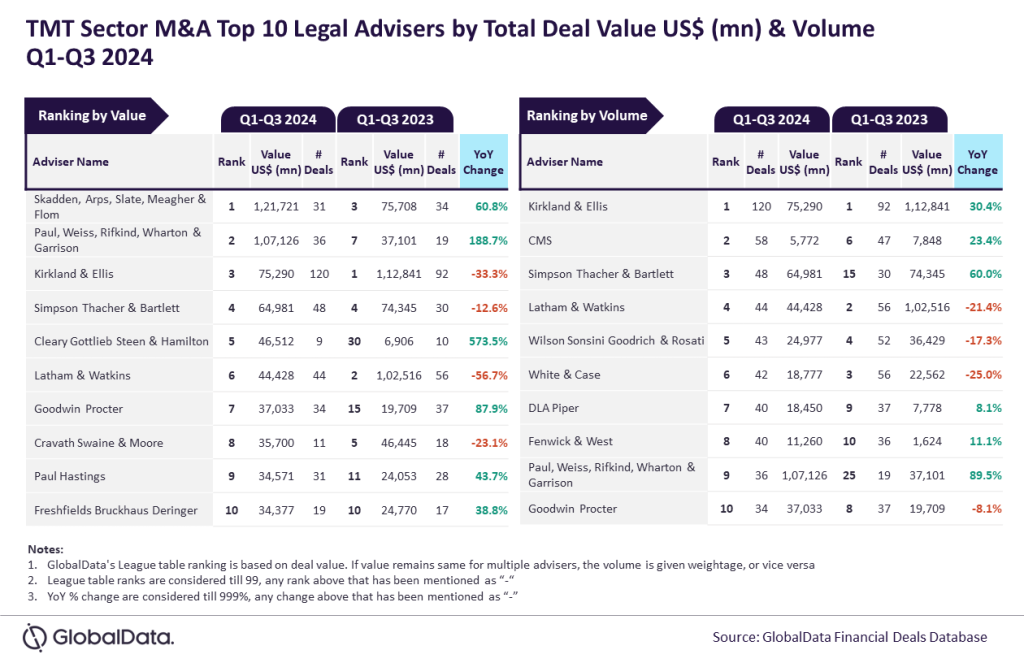
An unidentified hacker successfully gained control of a computer system controlling a water treatment plant in Oldsmar and attempted to contaminate the Florida city’s water supply.
On 5 February an operator at the Oldsmar water treatment plant observed a threat actor take remote control of the computer system and briefly change the sodium hydroxide level from 100 parts per million to 11,100 parts per million.
The plant operator immediately spotted the increase and lowered the sodium hydroxide to normal levels, thwarting the attack.
Also known as lye, sodium hydroxide is the main ingredient in liquid drain cleaners and used to remove metals from water in treatment plants.
The targeted treatment plant provides water to some 15,000 residents in the city of Oldsmar, near Tampa.
“This is obviously a significant and potentially dangerous increase,” said Oldsmar Sheriff Bob Gualtieri during a press conference on Monday.
How well do you really know your competitors?
Access the most comprehensive Company Profiles on the market, powered by GlobalData. Save hours of research. Gain competitive edge.

Thank you!
Your download email will arrive shortly
Not ready to buy yet? Download a free sample
We are confident about the unique quality of our Company Profiles. However, we want you to make the most beneficial decision for your business, so we offer a free sample that you can download by submitting the below form
By GlobalDataA criminal investigation involving the FBI and US secret service is underway. There are no suspects as of yet and officials said they did not know if the cyberattack originated from within the US or externally.
“Because the operator noticed the increase and lowered it right away, at no time was there a significant adverse effect on the water being treated,” said Gualtieri. “Importantly, the public was never in danger”.
Gualtieri added that it would have taken between 24 and 36 hours for the contaminated water to hit the water supply system and that there are other safeguards in place that would have prevented the poisoned water from reaching residents.
The cyberattack happened at 1:30pm local time and followed an initial intrusion at 8am that Friday morning. The water treatment operator noticed the mouse being moved to “open various software functions that control the water being treated in the system”, Gualtieri said.
The hacker – or hackers – gained control of the Oldsmar water treatment computer system using the TeamViewer software, which is used by IT teams to provide remote technical support.
According to TeamViewer’s website, the software has been installed on 2.5 billion devices worldwide.
A TeamViewer spokesperson told Verdict that it doesn’t have “any indication that our software or platform has been compromised” and that the firm is “monitoring the situation very closely”.
“As a global remote connectivity provider, we have leading security measures and state-of-the-art authentication options in place,” the spokesperson said.
“TeamViewer stands ready to support relevant authorities in their investigation of the technical details such as how the cybercriminals potentially obtained login credentials, which are set and encrypted solely on the device. Generally, TeamViewer condemns any malicious behaviour on its platform.”
Tim Erlin, VP at cybersecurity firm Tripwire, said it was a concern that the attacker was able to authenticate into the remote access software.
“That entry point should be very well protected, given that it provides access to such obviously sensitive capabilities,” he said. “Protecting remote access into industrial systems where these types of changes can be made should be a high priority for any industrial environment.”
Oldsmar water supply hack exposes critical infrastructure vulnerability
The Oldsmar water supply hack is an example of a critical infrastructure cyberattack.
Among the most notable critical infrastructure hacks is the 2015 attack against the Ukrainian power grid, which resulted in about 230,000 people being left without electricity for one to six hours.
Such attacks are rare against the backdrop of an endless barrage of phishing emails and scams. But it is the type of cyberattack that has long kept security professionals up at night due to the potential to cause physical harm.
“The attack against Oldsmar’s water supply is precisely the kind of assault on critical national infrastructure that cybersecurity experts have been fearing for years,” said Stuart Reed, UK director of Orange Cyberdefense.
“It is frightening to think what might have happened if it was not for the vigilance of one of the plant’s operators.”
The Oldsmar hack also raises questions about the level of internet access critical national infrastructure and industrial control systems should be given.
Karl Sigler, senior security research manager at cybersecurity firm Trustwave, said that critical national infrastructure such as water supply plants should have “very limited, if any, internet access”.
“User accounts and credentials used to authenticate locally on the workstation and for TeamViewer should be changed frequently and utilise multi-factor authentication,” he added.
“In this instance, it was lucky that the user was physically there to see the remote control and what settings had changed, but all critical activities should be audited, logged and monitored for abuse.”
Jake Moore, cybersecurity specialist at internet security firm ESET, said:
“One of the best ways to run a company network is to constantly think like a hacker. Connecting systems to the internet that have the potential to cause critical changes with relative ease is asking for trouble. Luckily, they had redundancies in place that would have made a fatal outcome unlikely.
“However, whenever anything is connected to the internet there is a level of vulnerability, especially if remote tools such as Teamviewer are set up. Segregating networks for maximum security is vital.”
Read more: Elexon cyberattack: No blackout but supply chain vulnerability exposed