
Cybersecurity researchers have uncovered a malware campaign targeting Syrian citizens that uses Covid-19 to lure users into installing apps onto their phones that are then used to spy on them.
Discovered by researchers from cybersecurity company Lookout and detailed in a blog post published today, the campaign is thought to be being conducted by threat actors with nation-state backing, meaning they are acting on behalf of the Syrian government.
The surveillance malware, also known as surveillanceware, was found across 66 different malicious apps for Android. None of these were available via the Google Play Store, but instead are likely to have been distributed via third-party websites and app stores.
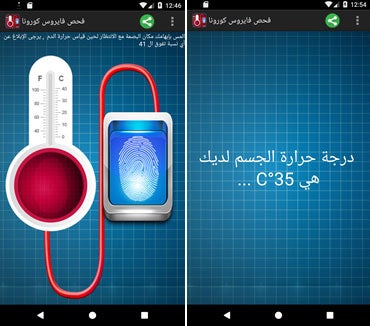
While all were presented to would-be installers as related to the Covid-19 coronavirus, only some of the apps targeting Syrian citizens contained functional applications. One which did was a prank app that claimed to test the user’s temperature, only to always show it as 35°C.
These were created using commercially available surveillanceware, which has been purchased and customised to give it a coronavirus theme and encourage its installation and use.
“Commercial surveillanceware like SpyNote, which makes up the majority of samples in this campaign, are customisable,” said Kristin Del Rosso, security research engineer at Lookout.
How well do you really know your competitors?
Access the most comprehensive Company Profiles on the market, powered by GlobalData. Save hours of research. Gain competitive edge.

Thank you!
Your download email will arrive shortly
Not ready to buy yet? Download a free sample
We are confident about the unique quality of our Company Profiles. However, we want you to make the most beneficial decision for your business, so we offer a free sample that you can download by submitting the below form
By GlobalData“The actor can make the app name and icon whatever they please. Sometimes, they even include functional applications inside the malicious app so the user is not suspicious, like with the Covid-19 temperature reading application.
“In other samples however, the actor did not include any useful functionality, so the application just spies on the user in the background.”
Syrian government using Covid-19 malware to support internet censorship
The surveillanceware campaign is thought to be latest effort by the Syrian government to censor citizens, particularly those acting against it.
“Based on past activity from this suspected actor, and the typical modus operandi of nation-state attacks, it is plausible that the goal is to spy on Syrian political activists,” said Del Rosso.
“Syria has an extensive history of internet censorship, and has gone as far as shutting down the country’s internet in 2011 and 2013.
“The pro-government hacking group, the Syrian Electronic Army, who is likely behind this mobile campaign, has repeatedly hacked websites to post pro-Assad messages, and retaliated against sites that did not cover him favourably. In the past, this group has targeted journalists and human rights activists that did not agree with the government, so this type of campaign is not unprecedented.”
The Covid-19-themed malware currently being used to target citizens is the latest iteration in a years-long campaign that is designed to spy on Syrian citizens, with the threat actor thought to be taking advantage of the desire for information about the coronavirus to encourage users to install the infected apps.
“The campaign has been active for years, but it only started recently taking advantage of the current media coverage around coronavirus to use it as the newest lure,” explained Del Rosso.
“Older samples from this campaign impersonated a variety of applications that might be of interest to potential targets, so it makes sense that the newest applications are prey on the fears of this health crisis, so that they have a higher chance of being downloaded.”
And while this campaign is only thought to be targeting Syrian citizens, Del Rosso does anticipate similar malware campaigns that take advantage of Covid-19 interest to be enacted in other parts of the world.
“We’ve seen similar campaigns run in multiple countries for years, especially in regions with less protections around freedom of press and free speech.”
Read more: Ten-year Chinese hacking operation targets Linux servers




